Software Solutions
The CyberShure software solution offering is scalable, easy to understand and quick to implement which gives immediate time to value.
Speak To SalesFILE ENCRYPTION
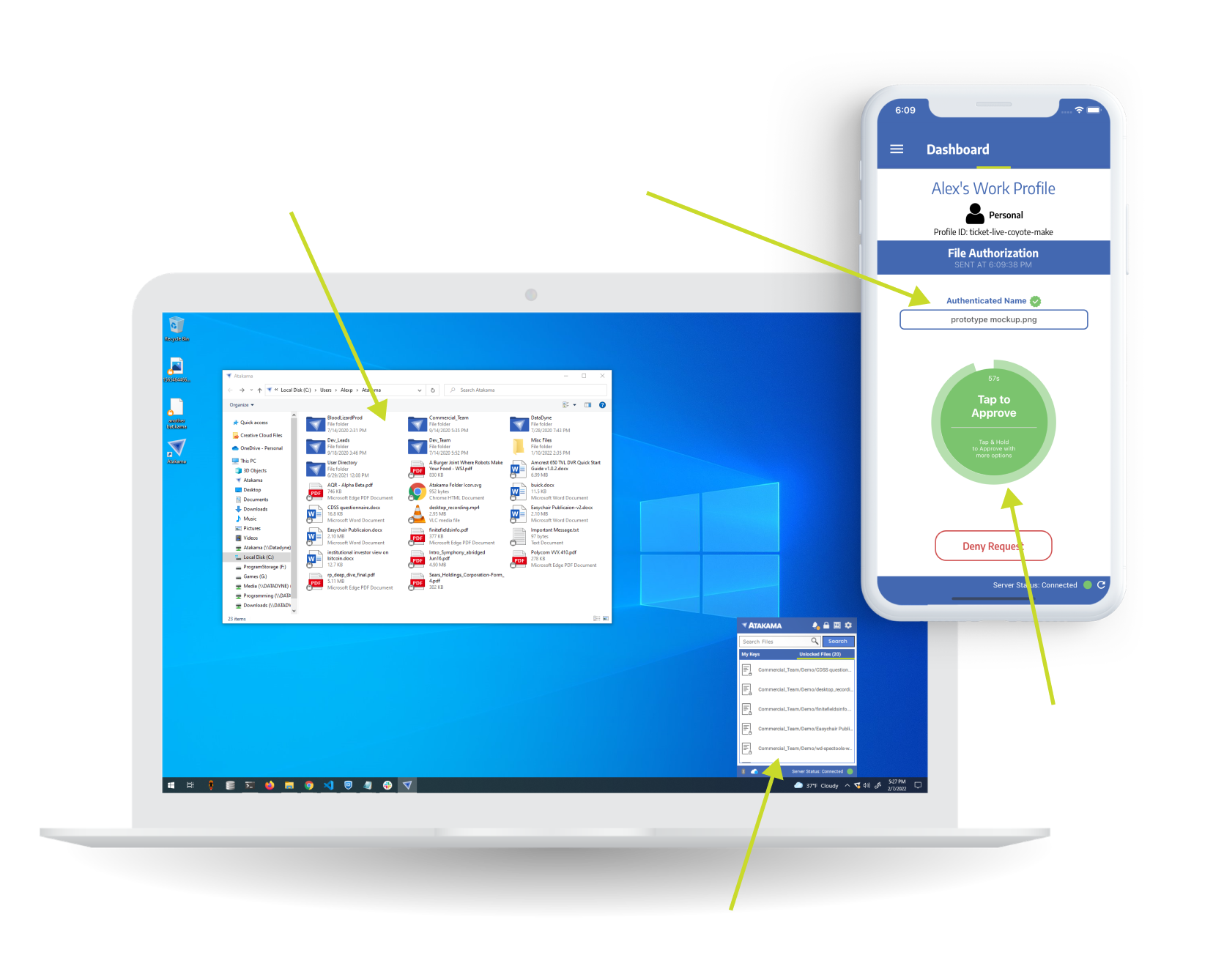
Atakama
Enhanced Information Security Through Multi-Factor Encryption | One-of-a-kind information security solution designed to keep business data safe from attacks, even when other security fails. Atakama offers customizable security policies to fit your business needs and user workflows.



CLOUD APPLICATION RESILIENCE
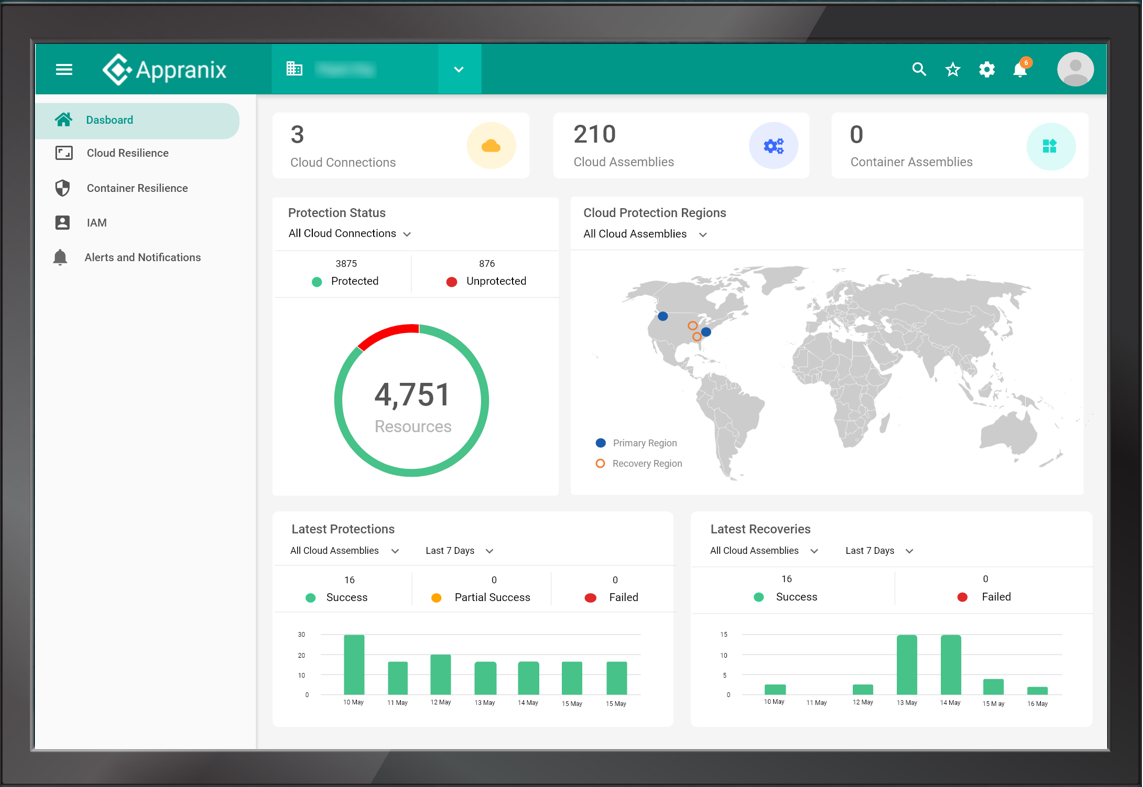
Cloud Rewind
Commvault Cloud Rewind empowers enterprises to achieve cloud application resilience against any cloud application downtime. Appranix's unique approach delivers unprecedented resilience for distributed and dynamic cloud workloads.



BLUE TEAM AUTOMATED THREAT HUNTING
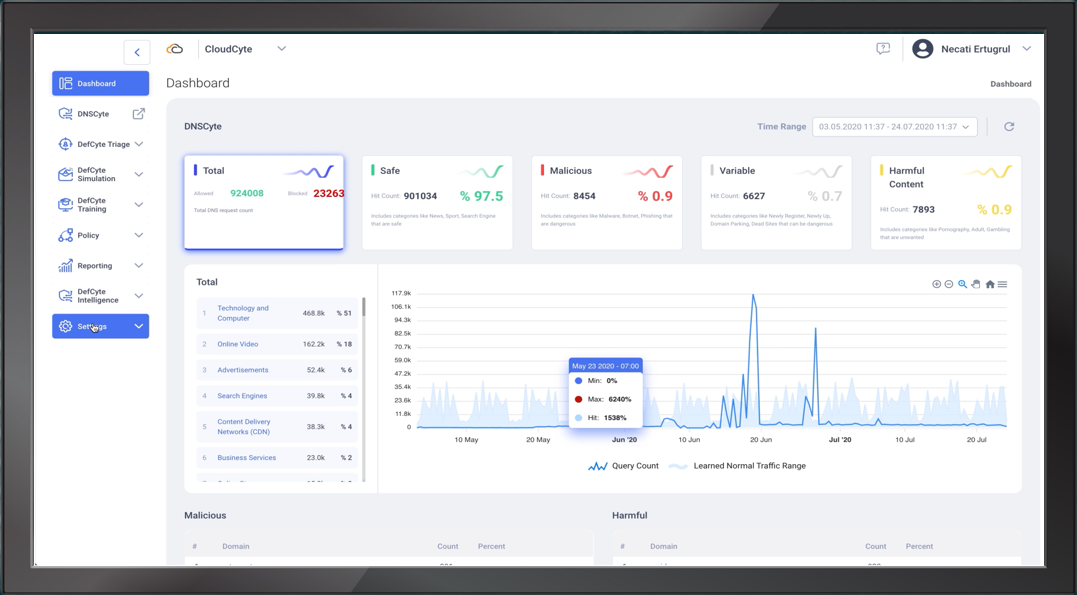
CyberCyte
CyberCyte provides a new layer of asset attack surface management and threat hunting framework for identifying and blocking hidden cyber threats living in stealth mode before compromising any infrastructure. The platform monitors all communication from end-users, data centres, cloud platforms, e-mail applications and OT devices to block any unverified communication attempts.



INFORMATION RISK MANAGEMENT
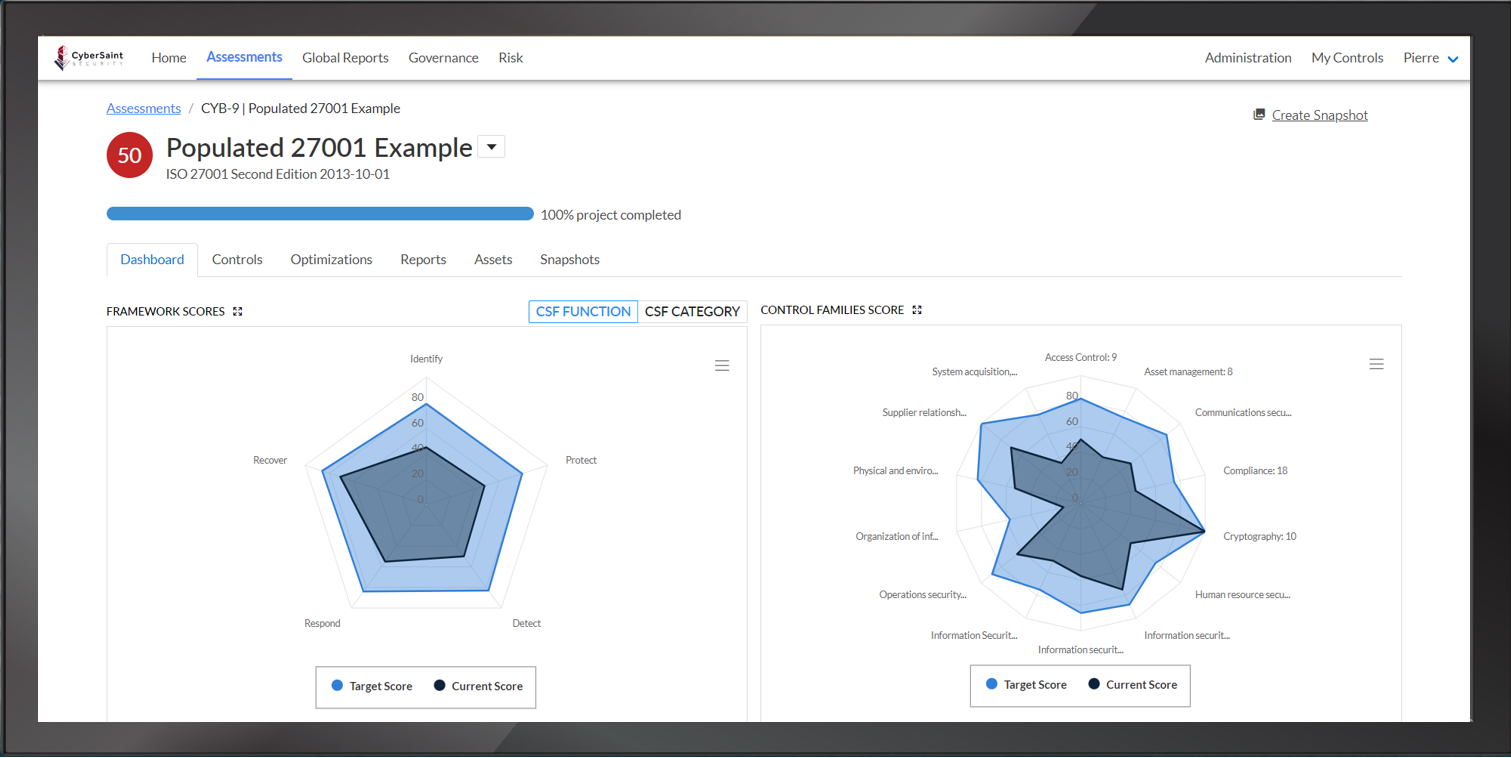
CyberSaint
The CyberStrong platform provides unparalleled visibility into risk, automates IT compliance, and creates resilience from assessment to Boardroom. CyberStrong automates compliance and risk assessments as data in your security tech stack changes.



APPLICATION CODE ANALYSES
DerScanner
DerScanner is a high-tech comprehensive application security solution that combines static (SAST), dynamic (DAST) and software composition (SCA) analysis methods in a single interface. DerScanner allows the identification of vulnerabilities and undocumented features in the code of mobile and web applications.

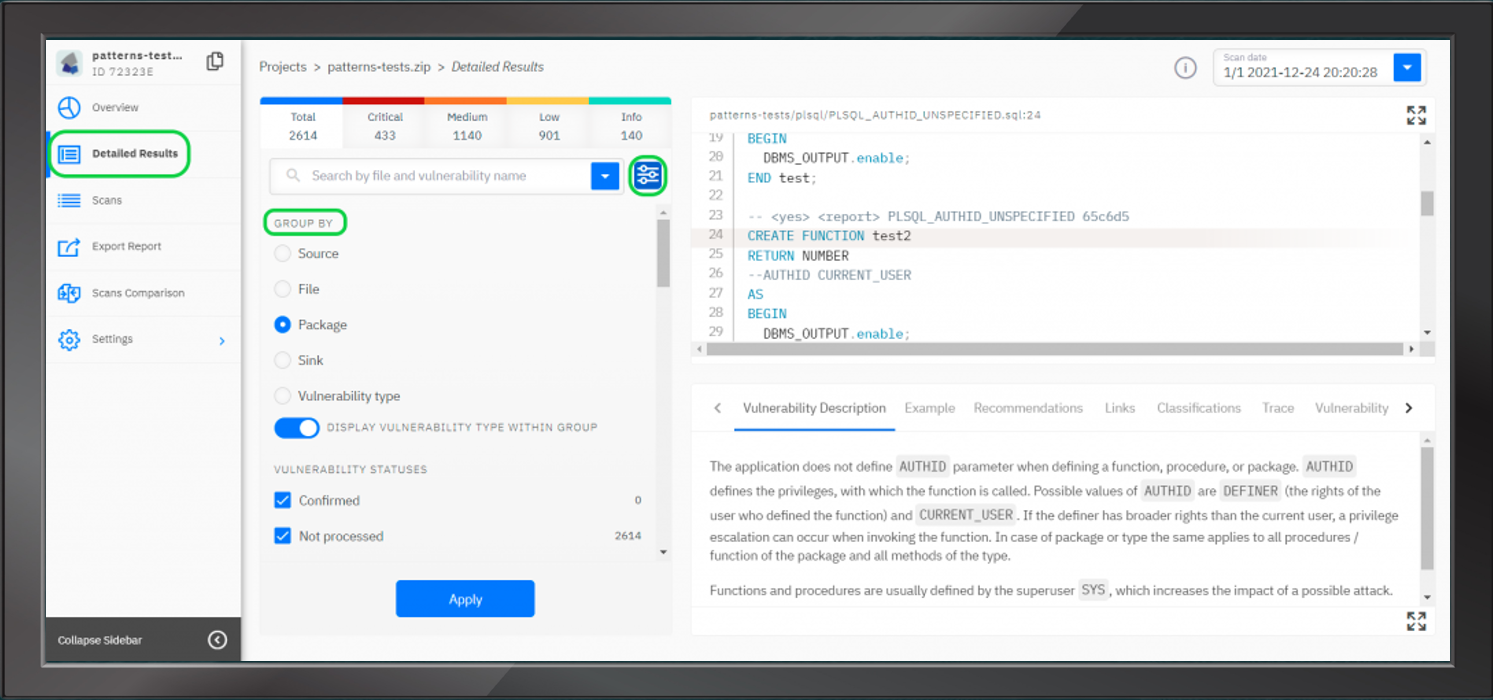


PRIVILEGED ACCESS MANAGEMENT
Fudo Security
Fudo Privileged Access Management (PAM) software help secure, control, manage and monitor privileged access to critical assets. By centralizing privileged credentials in one place, Fudo can ensure a high level of security for them, control who is accessing them, log all accesses and monitor for any suspicious activity.

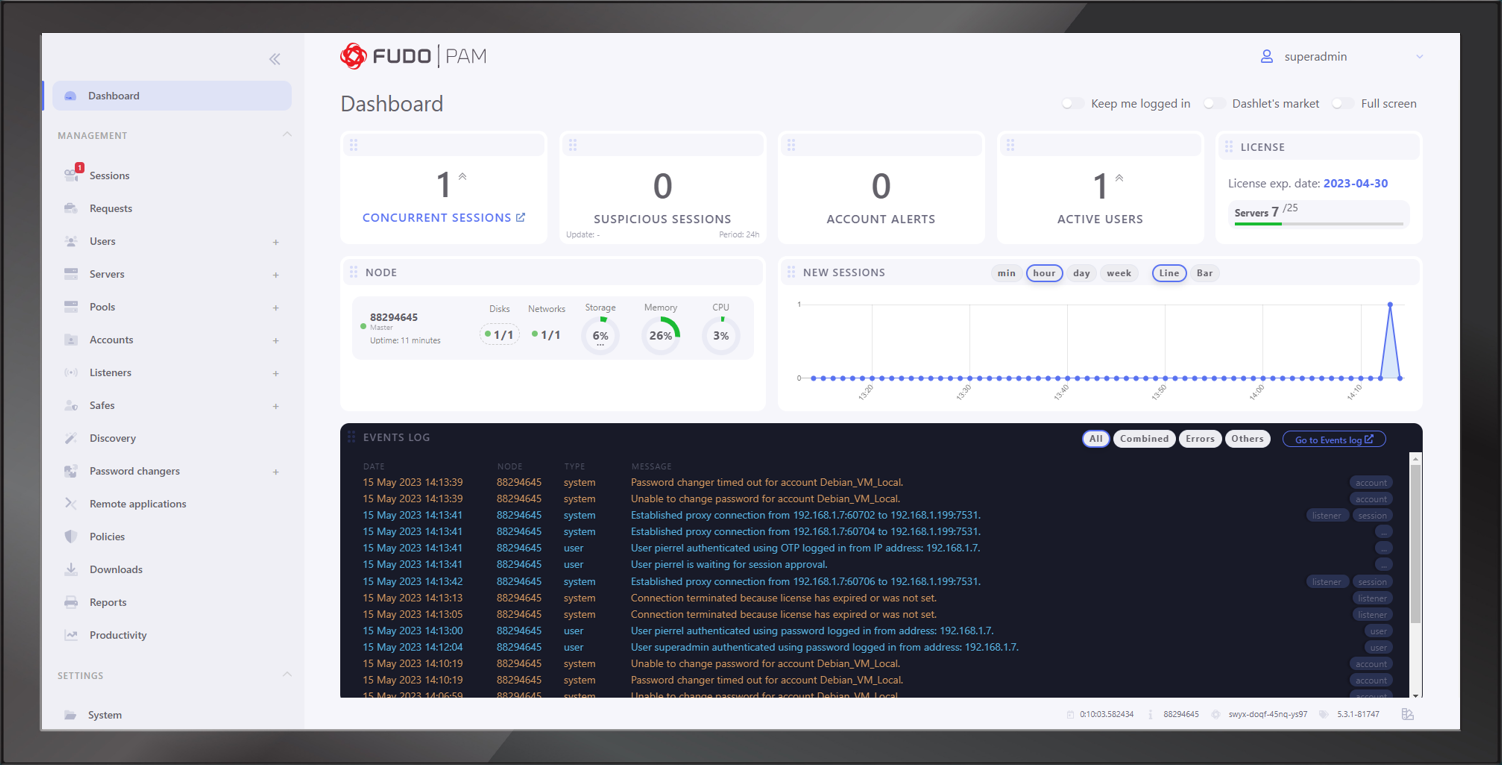


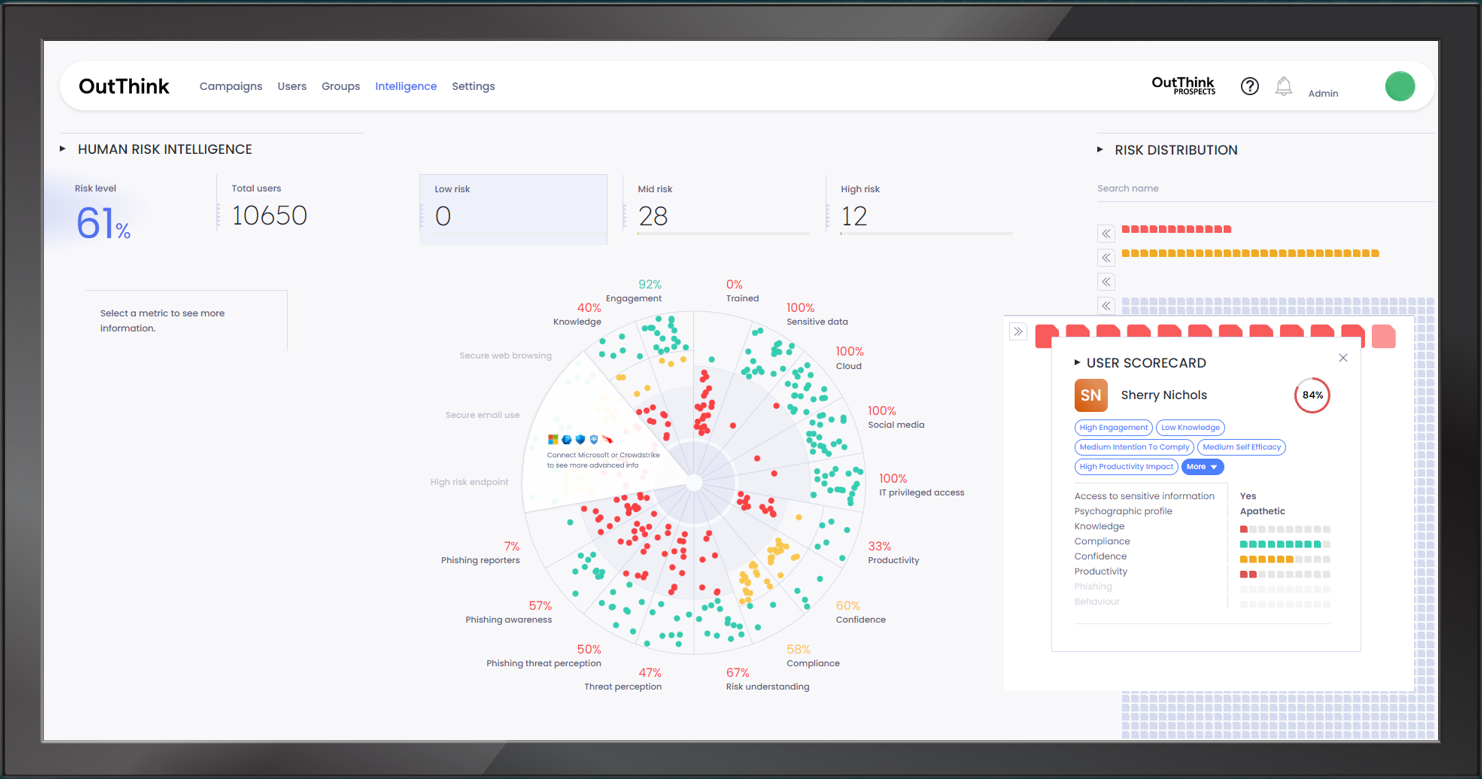
HUMAN RISK MANAGEMENT
OutThink
OutThink is a revolutionary Human Risk Management Platform (SaaS) empowering CISOs by targeting the source of 90% of all data breaches: human behavior. OutThink starts by turning security awareness on its head: targeted training that not only educates but allows you to learn from your people.



Lean On The Experts
You don’t have to do it alone. Our team of experts is waiting to help you.
Get Started
